Cyber Security
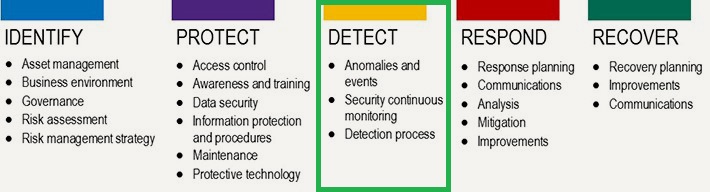
Where we intervain "DETECT"
-| Cybersecurity is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access.
-| Cybersecurity involves protecting information and systems from major cyberthreats, such as cyber terrorism, cyber warfare, and cyber espionage.
-| Cyber security, also referred to as information technology security, focuses on protecting computers, networks, programs, and data from unintended or unauthorized access, change, or destruction.
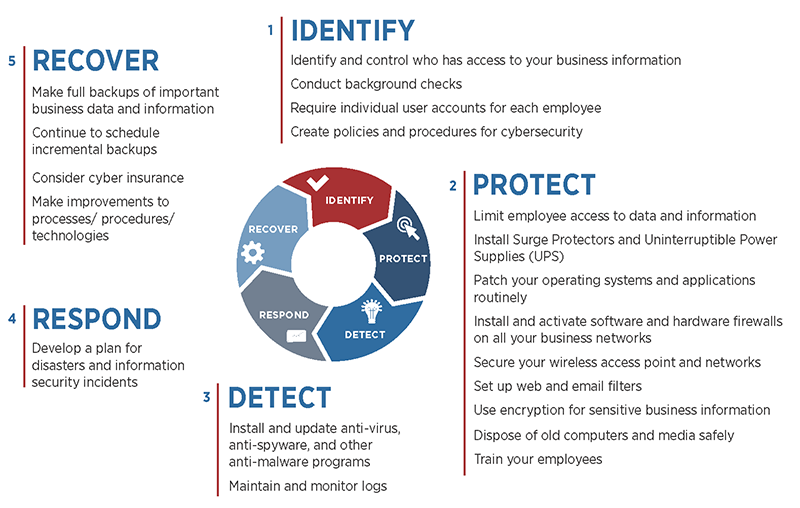
CyberSecurity Process Flow
Introducing Intrusion Detection (IDS)
> Have you ever wondered what was happening on your network at any given time?
> What about the type of traffic trying to get to a server on your network?
> Also do you have an idea of the type of transactions or traffic going IN and OUT of your host application servers?
Intrusion detection is the act of detecting events that have been deemed inappropriate or unwelcome by the business, organizational unit, department, or group. This can be anything from the emailing of company secrets to a competitor, to malicious attacks from a host on the Internet, to the viewing of inappropriate Web content during your lunch break.
Intrusion detection can be performed manually, by inspecting network traffic and logs from access resources, or automatically, using tools. A tools used to automate the processing of intrusion-related information is typically classified as an intrusion detection system (IDS).
IDSs act as security guards deployed throughout your network. An IDS watches for intruders on your network in the form of malicious users, bots, and worms, and alerts you as soon as the intrusions are detected.
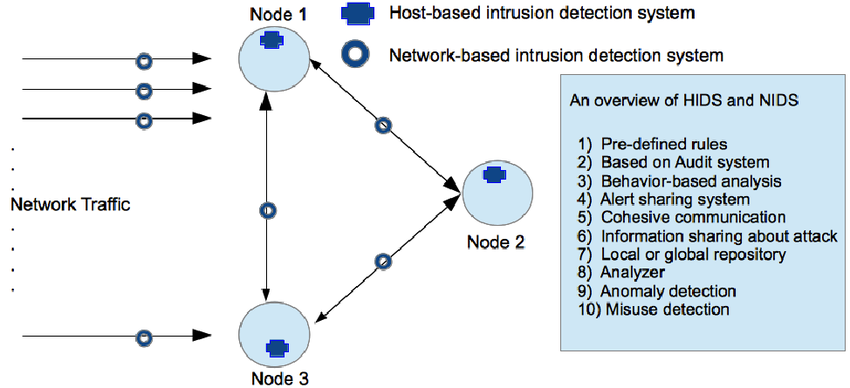
The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of a HIDS, while a system that analyzes incoming network traffic is an example of a NIDS.
A HIDS is designed to protect the server on which it is installed. It is able to inspect the full communications stream between the local and remote system interacting with the Host system.